| Table of Contents |
|---|
Introduction
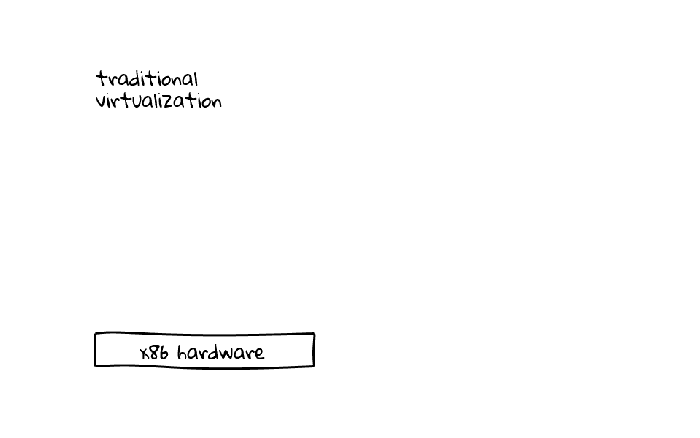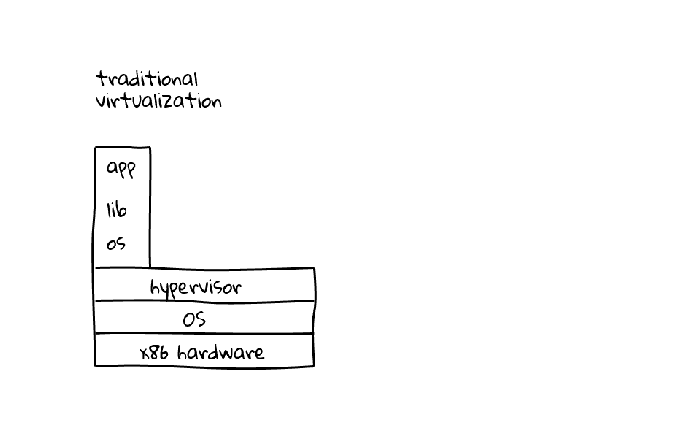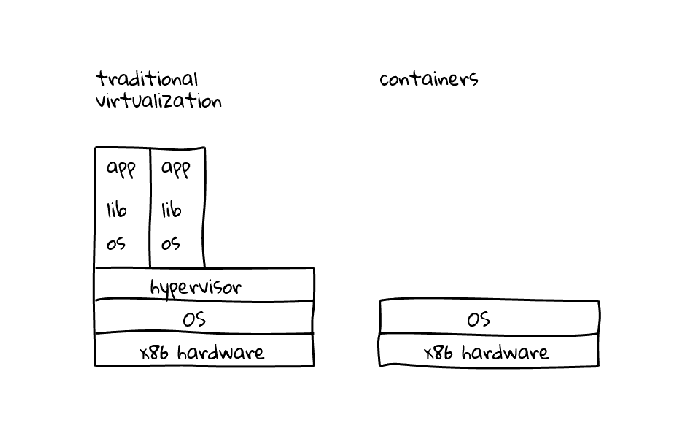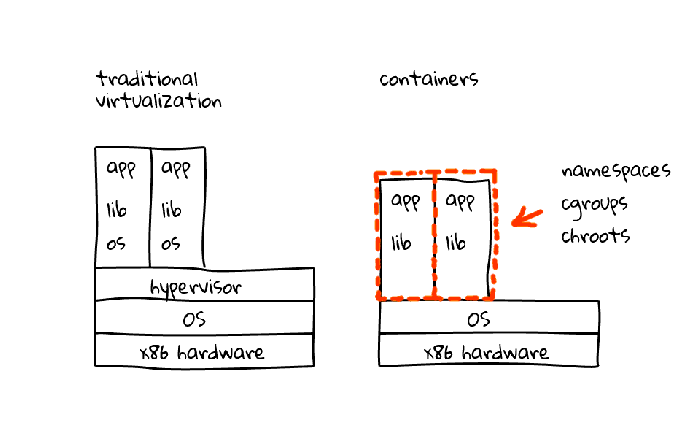
Below image shows the key difference between traditional virtualization and containers,
Why Use It?
LXC is in between a VM and a pure application container. It will take up more resources than a pure container, but unlike a VM use as much memory as needed. It will provide a full kernel and OS (albeit it must be Linux). Unlike a VM, LXD container will have access to the resources and speed of the hardware without needing to emulate hardware. If you are interested in Docker or Cloud, not yet ready to give up your ssh console, start here. Learning LXC, you'll also really understand how Docker and Cloud works under the hoods.
...
| Attribute | Size | Comment |
|---|---|---|
| Disk Space | 337 MB | That's the entire operating system because it can mount shared core kernel files from the Host. Better yet as Read-Only |
| Memory (externally viewing Container) | 12.96 MiB ~ 1.7 MB | Using lxc-info which excludes the shared kernal memory |
| Memory (Inside Container) | 5.6 MB | Smaller hence because the container leverages the host OS. Note, need to speak to LXC guys to understandy why external versus internal difference. |
| Processes (Inside Container) | 15 | Container leverages the host OS. |
Limitations
There are some kernel functionality that cannot be used inside of a container,
- Firewall
- Mounting External File Systems - Instead Mount in the host OS and then share to the container
Install
Install LXC,
| Code Block | ||
|---|---|---|
| ||
sudo apt-get install lxc |
...
| Tip |
|---|
Best to use your own Linux machine, but if in a pinch, you can try it out on the Linux Containers website for free. |
Create Regular Privileged Container
The simplest to implement container is a privileged container. In other words, the user and process running the container is root. This is not as bad as it seems from a security perspective and easiest to manage (so far). Tin to talk to Dickson to find out if Solaris (which is more mature with container technology) started using unprivileged and if so will look into that next for Linux.
Container Derived from Image File Downloaded to Base OS
This draws the files from the existing image matching downloaded from the Base OS to make your container. Note the image file must be compatible (for now) with the Base OS. I observed it may also be looking at details of your Host OS as the process creates accounts in the image that matched Host OS. The image folder was created/downloaded during the lxc setup and resides in /var/cache/lxc/trusty/rootfs-amd64. The template file to create the container resides in /usr/share/lxc/templates/,
...
| Code Block | ||
|---|---|---|
| ||
sudo lxc-ls --fancy NAME STATE IPV4 IPV6 AUTOSTART ------------------------------------------ app STOPPED - - NO # look at the stopped container sudo lxc-info --name my-container Name: my-container State: STOPPED |
Sparse Container from Host OS
Not sure if this functionality exists yet. Solaris has a concept of a sparse root zone which I would call here sparse container. The idea to reduce scope overhead so that aside from basics (home, opt, temp) the rest of the file system is actually mounted as read-only from the Host OS. In this model we have tighter security with minimal packages.
File Structure
You will need to use sudo or root to view the directories. I use root,
...
See lxc.conf(5) for additional configuration options on the above files.
Container Networking
By default, LXC creates a private network namespace for each container using a DHCP server (dnsmasq), a NAT server (package name?) and configures IP Tables masquerade entries for outbound network access.
In other words, containers exist within a private network, may see each other, pull network data to whatever the host can access, but nothing outside aside from the host itself will see these servers. A good analogy is your home network behind 1 public IP given on your service provider router.
Enabling LXC DNS Resolution
By default, the containers can only see each other by IP addresses. DNS resolutions by default is not enabled.
I'm not going to show how to fix this because we will get this out of the box when graduating to using LXD.
Static LXC Assigned IP
When working with servers, without orchestration, it is best to use static IPs. This should be your first step if seriously using containers for production use. By default, LXC assigns an internal set of IPs within the range of 10.0.3.2 to 10.0.3.254 which is defined in /etc/default/lxc-net.
...
You may alternatively set the container OS itself to use static using the interfaces file.
Making Containers Available on the Network
Containers may also be made available on the larger network which is covered in 5.1 LXC with Advanced Networking.
Start Container
This starts the container as a process,
...
For troubleshooting, you may omit --daemon which will run the containers as an actual program where you can see the container booting up.
Logging In
Console
Replicate loading console,
...
Make to change the password for the default user or delete the default user when you create your own accounts.
Simulate Terminal
There is another way of getting in (good for initial setup without default accounts or emergencies),
...
lxc-attach is used to execute an arbitrary command inside a container that is already running from outside the container. Because nothing was specified, you end up running bash inside of the container.
Container Management Key Commands
Here are some of the key commands for container management,
...
| Code Block | ||
|---|---|---|
| ||
# snapshot # rename |
Cloning a Container
One of the most exciting aspects of containers is being able to clone (duplicate).
Clone
Shutdown (not entirely sure if needed but I do as principle) your container and clone from the host,
...
If you want to just try things you, you will want to look at snapshots.
Clear Out Old Data
Log Files
If you need to be enterprise class, clear out your new cloned containers log files which will reference the original container hostname. Here is an example search on a relatively new container,
...
There's more... user history...
Regenerate SSH Host Keys
Next boot up your container, log via the lxc console (is less steps) or ssh with a sudo enabled account and change your SSH host keys,
...
| Code Block | ||
|---|---|---|
| ||
ssh-keygen -R remote-server-name-here |
Mounting a Network Folder
You can't at this moment (March 2016) and I understand this is because it is a shared kernel issue. Solaris does not allow this either if I recall.
Instead use your host to mount your network folder and then share your host folder as described in the next section.
Share Folders with Host
In this example, we want to mount a shared directory from the host system to be accessible to one or more containers,
...
| Note |
|---|
If your host is mounting another folder (ie a network share). You must mount in your host first then start your container. |
Moving Container to New Host
... (this will probably be a separate article)
...
https://www.stgraber.org/2013/12/20/lxc-1-0-blog-post-series/
Setting Up Zero Footprint 32-bit Java on LXC 64-bit
By default, the apt-get packages inside of the the containers only use 64-bit architecture,
...
Then follow-up with installing the proper dependencies, but not sure if I need to install in the host... need to try this out in a VM.
References
Good overview of lxc - https://www.flockport.com/lxc-vs-docker/
...